icon.
icon.You must fix all vulnerabilities that cause hosts to fail compliance. These vulnerabilities are marked with the  icon.
icon.
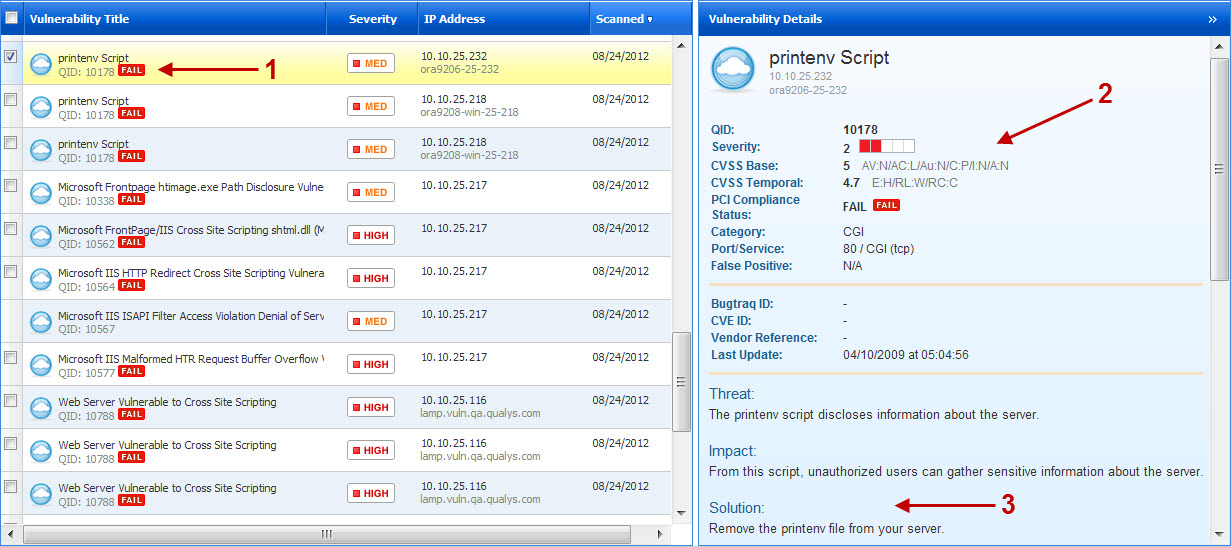
The Current Vulnerabilities list (Network > Vulnerabilities) displays all the vulnerabilities detected by the latest scans of your network. To view the vulnerabilities list for a specific scan, go to Network > Scan Results, and click the View Vulnerabilities icon  on the scan row.
on the scan row.
1) Click a vulnerability row showing the  icon to display the Vulnerability Details. 2) View the vulnerability details. 3) Scroll down to Solution for suggested fixes for the vulnerability.
icon to display the Vulnerability Details. 2) View the vulnerability details. 3) Scroll down to Solution for suggested fixes for the vulnerability.
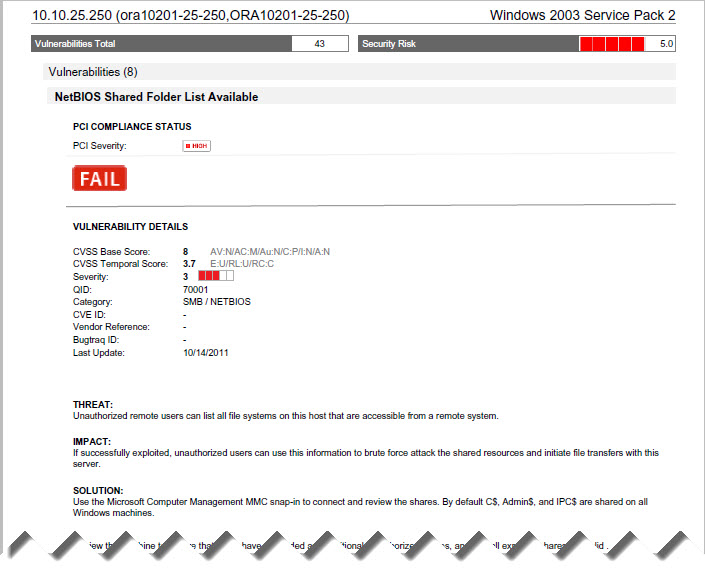
The PCI Technical Report is one of the two network reports that you can create from the Compliance section. The Detailed Results section of this report shows all detected vulnerabilities sorted by host. Vulnerabilities that must be fixed to meet PCI compliance are marked with the  icon. Scroll down to the Solution to learn how to fix each of these vulnerabilities.
icon. Scroll down to the Solution to learn how to fix each of these vulnerabilities.